Once we installed Zimbra Collaboration, we need to be aware of some additional configurations that will allow us to send emails to other Email systems with an improve Security, such Gmail, Hotmail, Yahoo!, etc. This Wiki article will show the different Email Protection resources that exists, depends of the volume of sent email, will be better to implement only one, or two, or maybe all of them, depends.
SPF
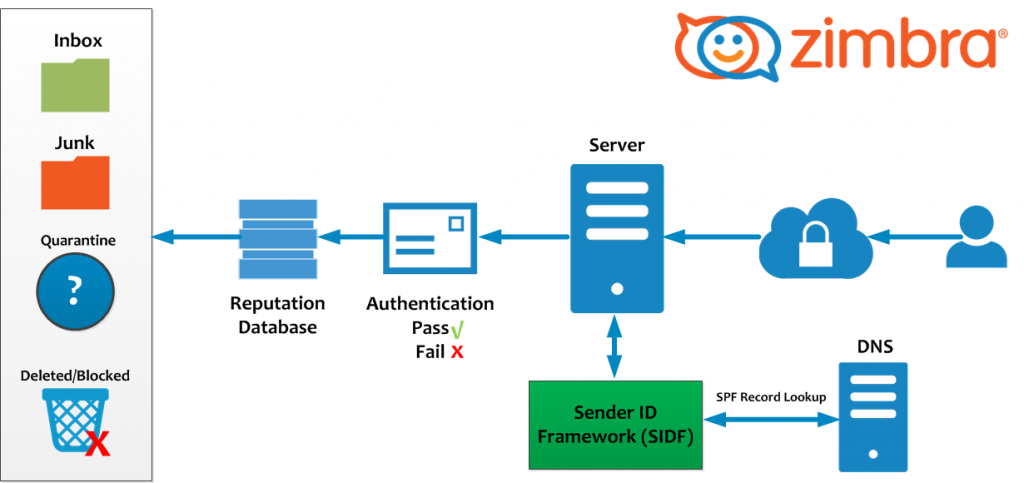
Sender Policy Framework (SPF) is an email validation system, designed to prevent unwanted emails using a spoofing system. To check this common security problem, SPF going to verify the source IP of the email and compare it with a DNS TXT record with a SPF content.文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
Where needs to be configured?
SPF needs to be configured in the Public DNS文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
How to configure it?
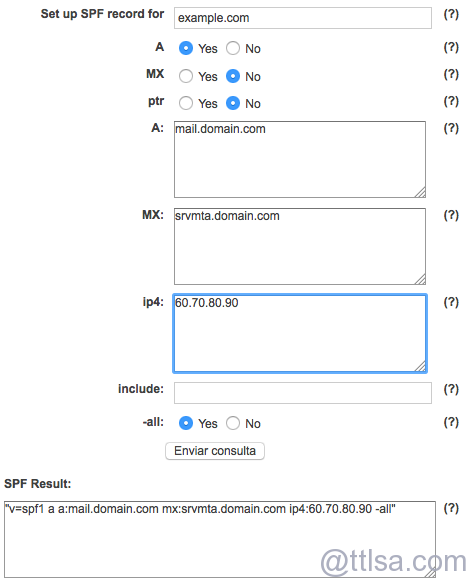
First of all, generate the TXT SPF DNS entry (using the Mailradar SPF Tool, or something similar), for example with the domain called domain.com and have 3 different entries to add:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
- The A entry - mail.domain.com
- The MX entry - srvmta.domain.com
- The IPv4 entry - 60.70.80.90
If in your email system you are using external services like Mailchimp, Salesforce, etc. add them in the include part, for example:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
- include:servers.mcsv.net (Mailchimp)
- include:_spf.salesforce.com (Salesforce)
- include:_spf.google.com (Google Apps)
An example will looks like:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
Understand the "all" feature in the SPF entry
SPF can be configured in different ways, since neutral to hard fail. Almost 98% of domains are using the ~all (softfail) that means even if something of the SPF entry is wrong against the source Mailserver, mark the mail only like softfail. Here, the complete table to understand the feature all in the SPF文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
| Parameter | Result | Means |
|---|---|---|
| +all | pass | Permits all the email, like have nothing configured. |
| -all | fail | Will only mark the email like pass if the source Email Server fits exactly, IP, MX, etc. with the SPF entry. |
| ~all | softfail | Allows to send the email, and if something is wrong will mark it like softfail. |
| ?all | neutral | Without policy |
Difference between ~all and -all
If your domain is under an SPAM attack trying to spoofing your domain, try to change the SPF to -all for a while, and reset to ~all when the attack ends. Keep selected the -all if you want to be strict with the SPF entry and you are sure that your DNS entry is correct.文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
How to test it
Have a lot of SPF tools to check if the DNS entry is correct, for example:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
- http://tools.wordtothewise.com/spf (will show an overview of all the allowed IPS that can send using the domain)
- http://www.kitterman.com/spf/validate.html (Simple but effective, will show the SPF DNs entry and also the result: pass, softfail, fail, neutral, etc.)
- http://mxtoolbox.com/ A Classic
Deprecated SPF RR, use TXT RR only
In April 2014, the SPF DNS record was deprecated in the RFC, and the correct way to implement the SPF is using only a TXT DNS record. For example, this was a valid DNS entries before April 2014, TXT and SPF:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
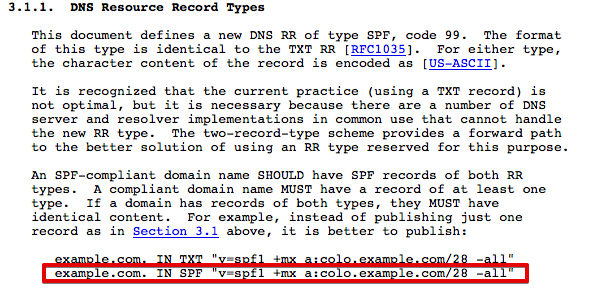 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
And here the RFC text where you can find the part about use only TXT:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
DKIM
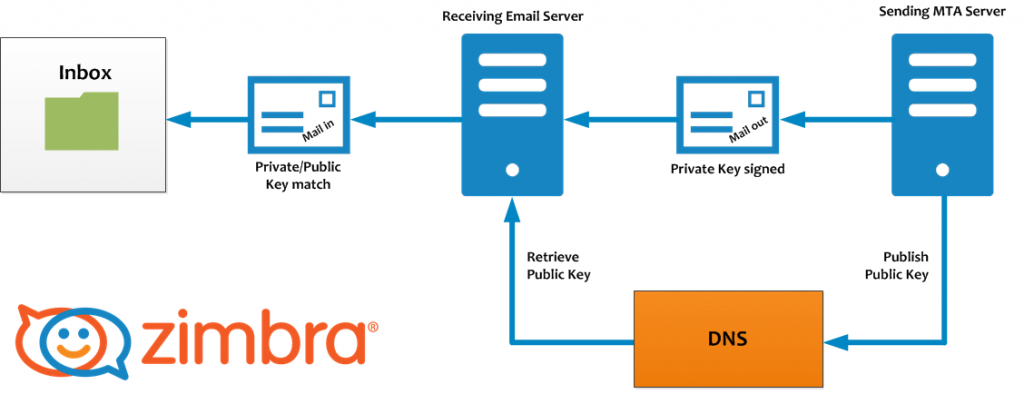
DomainKeys Identified Mail (DKIM), is a method to associate the domain name and the email, allowing to a person or company assume the responsibiltity of the email.文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
Where needs to be configured?
DKIM needs to be generated per domain in our Zimbra Server, and needs to be configured in the public DNS of each domain.文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
How to configure it?
To configure properly DKIM, please follow the next Wiki - Configuring_for_DKIM_Signing文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
Once have the DKIM generated in Zimbra, add the info in the public DNS, will looks like:文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
![]() 文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
文章源自运维生存时间-https://www.ttlsa.com/safe/best-practices-on-email-protection-spf-dkim-and-dmarc/
How to test it
Have multiple websites to test it, for example:
- http://dkimvalidator.com You need to send a email, once you have the DKIM configured, then in the website will found a section called DKIM and the result in the end, if the test is passed or not.
DMARC
DMARC, which stands for “Domain-based Message Authentication, Reporting & Conformance”, is a technical specification created by a group of organizations that want to help reduce the potential for email-based abuse by solving a couple of long-standing operational, deployment, and reporting issues related to email authentication protocols.
DMARC standardizes how email receivers perform email authentication using the well-known SPF and DKIM mechanisms. This means that senders will experience consistent authentication results for their messages at AOL, Gmail, Hotmail, Yahoo! and any other email receiver implementing DMARC. We hope this will encourage senders to more broadly authenticate their outbound email which can make email a more reliable way to communicate.
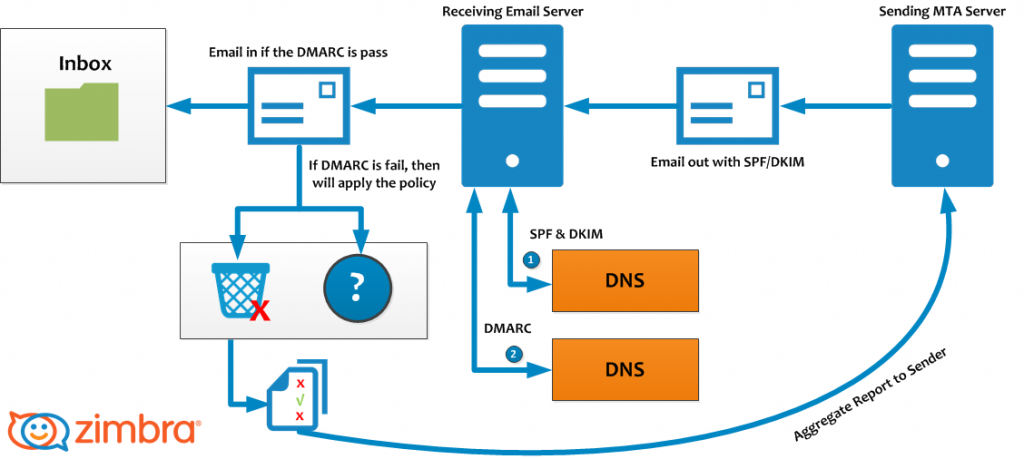
Text and Image inspided from the Official dmarc org website
Where needs to be configured?
The DMARC needs to be configured in the public DNS.
How to configure it?
The DMARC record can be generated in multiple websites, for example http://www.kitterman.com/dmarc/assistant.html
Using the domain example.com, a possible option can be the next, please note that all the default options will be included implicit, even if you don't select them in the generator:

This configuration will generate the next DNS entry
- DMARC record for: example.com
- Record should be published at _dmarc.example.com
- v=DMARC1; p=quarantine; rua=dmarc@example.com; ruf=dmarc@example.com; sp=quarantine
And will looks like this in a DNS with web interface:
![]()
How to test it
One of the best Sites to test the DMARC is the next link - https://dmarcian.com/dmarc-inspector/google.com is coming with the google.com domain per default. This website will show you all the DMARC information about your domain.
rDNS
The reverse DNS resolution (rDNS) is a determination of the domain name that is associated to an IP. Some email companies like AOL, for example, will reject any email that doesn't have a valid rDNS.
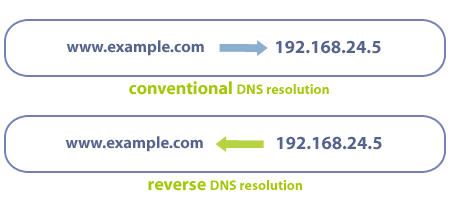
Where needs to be configured?
To have a perfect match between the rDNS and the SMTP Banner of the server, need to have the next:
- In the public DNS of the ISP provider. Or if you have control of the public DNS of your IP range, then you can add the rDNS by yourself.
- In the Zimbra Server, need to edit the HELO to match between it and the rDNS record.
How to configure it?
To modify the Public DNS to match the IP and the rDNS, you need to contact with your ISP provider, or if you have acces to edit the DNS record of your IP, then change it by yourself. For example, if you have the IP 60.60.60.60 and needs to resolve to mail.example.com.
To edit the SMTP Banner and match it with the external rDNS. Need to edit the next in Zimbra: Zimbra 8.0.X
zmlocalconfig -e postfix_smtpd_banner="mail.example.com" zmcontrol restart
Zimbra 8.5, 8.6, and above
zmprov ms `zmhostname` zimbraMtaSmtpdBanner mail.example.com zmcontrol restart
How to test it
Use the next tool - http://mxtoolbox.com/ReverseLookup.aspx and fill it with your Public IP, if you have everything well configured, will return the name that you want.



评论